BYOD, CYOD, COPE, COBO, COSU – how to understand and use mobile device strategy?
What do they mean?
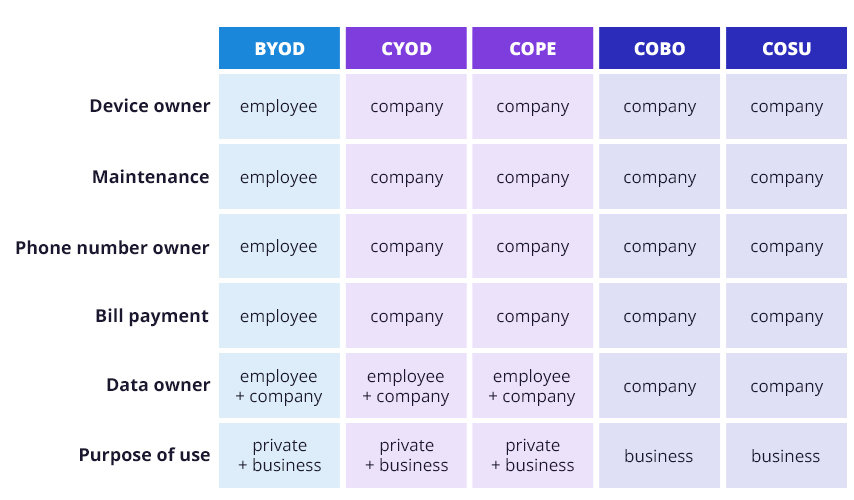
BYOD, CYOD, COPE, COBO and COSU are acronyms describing an organization’s mobile device management policies. They are also known as organizational mobility management models. The most straightforward criterion for their division is ownership.
We can therefore divide devices into personal devices used in the model:
- BYOD – Bring Your Own Device;
and company-owned devices (COD) used in models:
- CYOD – Choose Your Own Device;
- COPE – Corporate Owned, Personally Enabled;
- COBO – Corporate Owned, Business Only;
- COSU – Corporate Owned, Single Use.
What are the implications of this?
The owner of the device bears the cost of its purchase and maintenance. They also have the opportunity to choose the device they buy. The only bend to this rule is the CYOD model, where the company allows the employee to select the device from a defined list.
The phone numbers and SIM cards used on the carrier are closely linked to the device’s ownership. It is not practiced to separate these two aspects. As a result, the device’s owner also bears the costs of telecommunications services.
Another element, in the context of ownership, is the ownership of the data processed on the device. It’s related to the nature of its use. The BYOD, CYOD, and COPE models simultaneously use the device for both private and business purposes. This may raise concerns about data security, administration, or intermingling business and personal zones.
How do you create your policy?
It is worth starting with the needs. The models described above should be a guideline, not a rigid framework into which you have to fit. When choosing or creating a mobility management policy, it is worth starting by reviewing five key areas:
- The device: who chooses it, who pays for its purchase, who owns it, who is responsible for its maintenance, and who owns the data – what nature of use do we envisage for the device?
- Services: who owns the phone number and the SIM card, and who pays the ongoing telecoms bills – including roaming resulting from, for example, business travel?
- Management and support: who manages the device and is responsible for support? Here, it is worth remembering that only the installation of an MDM/UEM agent enables the device to be managed remotely and thus allows full support to be provided.
- Integration and applications: what level of integration into the corporate environment is required to maintain adequate workflow? Any broader integration, beyond essential tools such as mail or video conferencing, requires more work to implement and manage.
- Expectations vs. reality: which department will implement and maintain the policy? Whether the time needed to implement the policy will fit into the working time of existing employees? Do we have the proper management tools/systems?
Whether can you meet all expectations?
In a more complex structure, this cannot be easy. The solution is to balance the level of control and the flexibility of policy/model implementation. You will obtain the highest level of control by COBO and COSU, followed by COPE and CYOD, and at the very end, by BYOD. On the other hand, the BYOD model is the easiest to implement because when employees arrive at the company, they have a device to use in business operations.
There is no need to choose just one device or management model. Policies can change according to department, device, or area of operations. Regardless of the direction selected, creating specific policies allows for the organization’s and employees’ informed protection. A device management tool can make ensuring security and regulatory compliance easier and maintain expected productivity levels. It can even be essential in models that combine business and private space.
A professional MDM/UEM system will allow the creation of such a space and its security management and the deletion or erasure of data if required.
Grab some knowledge with Proget – check out some of our other articles:
- Cyber hygiene in business – learn the simple rules and how you can support it
 Cyber security is an important element of trust both in and within an organization. This is especially true at a… Czytaj więcej: Cyber hygiene in business – learn the simple rules and how you can support it
Cyber security is an important element of trust both in and within an organization. This is especially true at a… Czytaj więcej: Cyber hygiene in business – learn the simple rules and how you can support it - Why choose a vendor that is ISO 27001 certified?
 What is the standard and ISO 27001 certification? ISO/IEC 27001 is an international standard for information security management that defines… Czytaj więcej: Why choose a vendor that is ISO 27001 certified?
What is the standard and ISO 27001 certification? ISO/IEC 27001 is an international standard for information security management that defines… Czytaj więcej: Why choose a vendor that is ISO 27001 certified?
