Jump to:
By October 17, 2024, organizations must implement the requirements of the EU’s NIS2 directive, which introduces several cyber security obligations. It also significantly expands the scope of regulated sectors and entities.
What is NIS2? Find out if your business needs to adhere to it and how you can make it easier to comply with the new directive.
What is the NIS2 directive and its purpose?
NIS2 (Network and Information Security Directive 2) is a development of the 2016 NIS Directive, Europe’s first cybersecurity law.
It was created in response to the need to adapt current regulations to the rapidly evolving landscape of cyber threats and increasingly sophisticated attacks. The goal of NIS2 is to achieve a high, standard level of cyber security across the European Union and to strengthen the protection of critical infrastructure and services vital to society and the economy.
Key aspects of NIS2
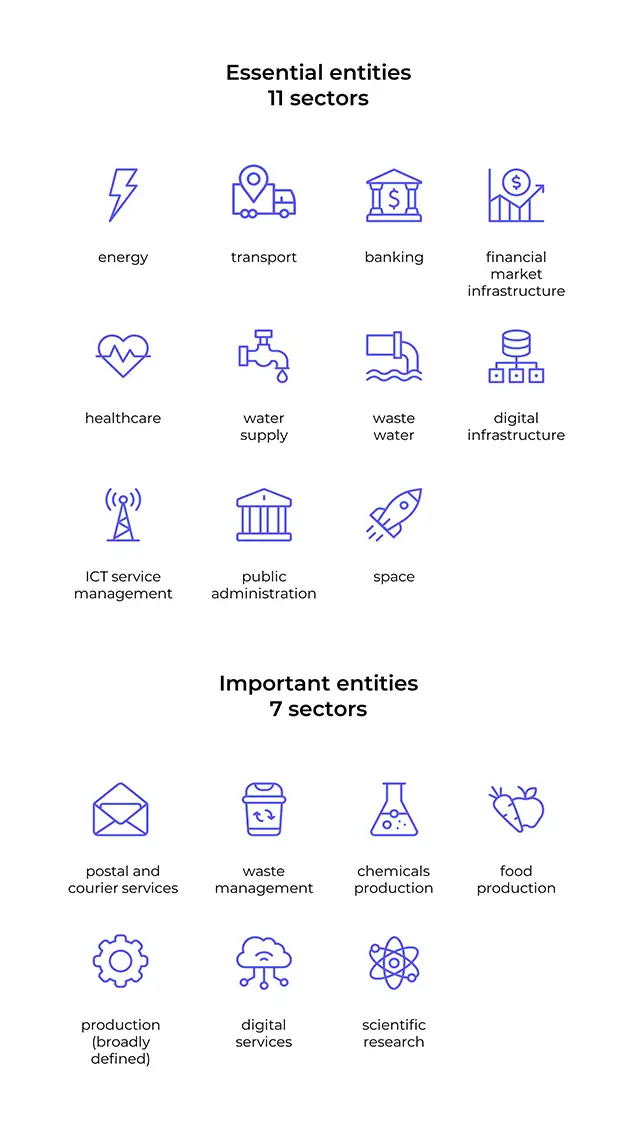
- Expanded scope – NIS2 covers more economic sectors than the previous directive, increasing the number of sectors from 7 to 18. As a result, more industries and entities are affected.
- New responsibilities – regulated organizations must implement minimum security measures to ensure effective risk management. In addition, NIS2 tightens incident reporting rules.
- Penalties and sanctions – the directive clearly specifies the amount of administrative penalties for evasion. They can reach up to €10 million or 2% of total annual turnover.
Who is affected by the new regulations?
NIS2 divides regulated companies into essential and important entities. The first group includes those whose disruption of operations, e.g., as a result of a cyber attack, could have severe consequences for the functioning of society and the economy (for example, energy, drinking water, banking). The second group includes companies of lesser but still vital importance (e.g., postal services, manufacturing).
What are the rules for identifying entities?
The directive lists the following criteria:
- Self-identification: the organization must self-assess whether it is subject to the directive and notify the relevant state authority.
- Size: the regulations apply to medium- and large-sized enterprises, i.e., those with more than 50 employees and an annual turnover or balance sheet total exceeding €10 million, among others.
- Area of activity: entities that provide services within the EU and operate in sectors deemed essential to the economy and society are subject to the directive.
New directive – new responsibilities
NIS2 introduces the exact minimum security requirements for all entities. Obligations under the directive are described in general terms, which gives flexibility in choosing solutions to help meet the objectives. In addition, each EU country can impose its regulations – provided they are no less stringent than those contained in NIS2.
What risk management measures need to be implemented?
The directive focuses not only on technical and organizational aspects of security. It also requires that employees be aware of the risks and adequately trained. Risk management measures should be adequate to the level of risk and cover at least these areas:
- Policies on risk analysis – procedures to identify, analyze, assess and minimize cyber security risks.
- Incident handling – procedures to detect, respond to, and prevent incidents.
- Business continuity – restoring normal operations of an organization after an emergency, such as through the use of backups.
- Security of networks and information systems – in the process of their acquisition, development, and maintenance, as well as handling the discovery of vulnerabilities.
- Security of the supply chain – establishing the requirements for external service providers.
- Security of human resources, asset management, and access control.
- Procedures for using cryptography, encryption, multi-factor or continuous authentication, secure voice, text, and video communications, and secure internal communications systems used in emergencies.
- Cyber hygiene – introducing its basic practices and regular training of employees in cyber security.

Reporting incidents
NIS2 tightens incident reporting requirements. Every essential entity must be ready to identify, respond to, and report cyber incidents quickly.
The most important obligation is to report serious incidents to the relevant CSIRT (Computer Security Incident Response Team) upon detection and without undue delay.
An initial notification should be sent within 24 hours of the detection of a breach, and more detailed information – up to 72 hours. The organization must provide a final report no later than one month after reporting the incident. The document should include a description of the incident’s course, the threat’s type and cause, and the countermeasures taken.
Administrative fines
There are legal and financial sanctions for non-compliance with NIS2 regulations. Legal sanctions can include, for example, compliance orders, implementation of security audit recommendations, and the obligation to inform customers of risks. Financial penalties vary depending on the category to which the organization belongs.
Essential entities: at least €10 million or 2% of total annual turnover.
Important entities: at least €7 million or 1.4% of total annual turnover.
Consequences, including financial and personal liability for non-compliance, may also be incurred by those in management positions.
Mobile device security as part of NIS2 compliance
Network and information system security is an essential aspect of risk management in light of NIS2. As digitization advances, business IT infrastructures cover an increasingly broad spectrum of devices, as reflected in the new regulations.
How does the directive define ‘networks and information systems’? It includes not just desktop computers and servers but any device that processes digital data (Chapter 1, Article 6). So mobile devices, such as laptops, cell phones, tablets, and amplified equipment, are also included.
Today, mobile devices are indispensable for conducting business, allowing employees to access applications, data, and resources from anywhere. According to NIS2, they must be appropriately protected – on par with traditional IT systems. Advanced mobility management solutions such as Proget are invaluable in accomplishing this task.

How does Proget support NIS2 compliance?
Proget is an All-in-One platform centralizing business mobile device management, monitoring, and protection. It helps IT administrators meet NIS2 requirements by offering various functionalities in the directive-regulated areas.
Full visibility and compliance
NIS2 requires constant monitoring of all mobile devices, which process corporate data and assess their associated risks. The Proget console includes a comprehensive inventory of equipment deployed to the system, providing knowledge of who has what devices and what they are. In addition, the solution enables ongoing tracking of mobile devices’ location and security status, dividing them into compliant and non-compliant with the organization’s established policies.
Incident handling and preventive measures
The directive mandates that effective procedures must be implemented to prevent, detect, and respond quickly to security incidents. Proget’s Mobile Threat Prevention Profile monitors devices, applications, and networks for potential threats. It also allows you to set up immediate, automatic responses to detected incidents – for example, an attempt to install a dangerous app. When a device is lost or stolen, administrators can remotely lock it or wipe corporate data, protecting it from unauthorized access.
Consistent and rigorous security policies
NIS2 obliges companies to develop and implement security policies, including for mobile devices. This extends to policies for the day-to-day use of equipment and methods of securing it. Proget allows you to configure consistent policies for individual devices or groups (such as employees in a particular department) and enforce compliance. Policies can impose, among other things, the need to set strong passwords, enforce encryption, and control access to device functions such as the camera or microphone. This approach minimizes the risk of typical security oversights, ensuring NIS2 compliance.
Effective application management
Since mobile apps often access corporate IT systems and data, they should be properly controlled, as they can become a source of security risks. Proget enables app whitelisting and blacklisting to block the installation of apps from unknown sources and minimize the risk of malware being installed on the device. The system also ensures that apps are regularly updated, eliminating security vulnerabilities from outdated, cyberattack-prone versions.
Your data in the right hands.

Summary
Although many companies are implementing cybersecurity policies and solutions mainly because of regulations, the market will likely soon impose these standards on its own, responding to rapidly evolving threats. Information security will become a key criterion for business cooperation, so it’s a good idea to implement appropriate protection measures now. Even if your company is not directly covered by NIS2, awareness of potential threats and a proactive approach to security is an investment that will ensure your organization’s future safety and stability.

Author: Agnieszka Pierlak
Marketing specialist with experience in the IT industry. Interested in issues related to cybersecurity and internal security. Privately, a lover of good literature, Asian cuisine and mountain hiking.
