Security policies
Consistent device usage policies – flexible and secure
Create your own policies or use pre-made ones
The Proget solution allows you to create and impose various policies that define the basic configuration and usage conditions of devices added to the console. The available policies depend on the operating system of the given device and, consequently, its activation type. When creating a new policy, you must specify its compatibility with one selected activation type. In Proget, you will also find a practical set of predefined policies configured appropriately for a chosen device activation type.
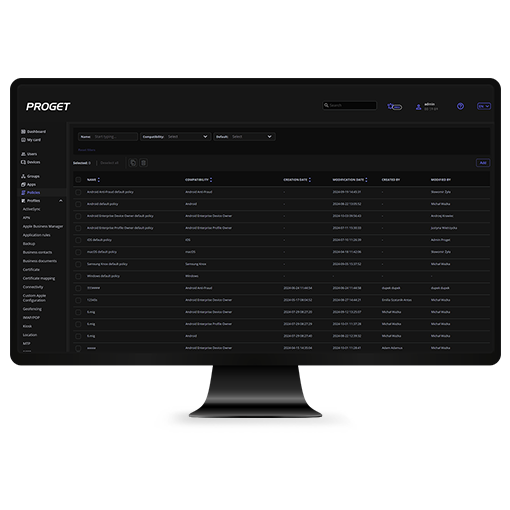
Assign policies sets collectively and remotely
You can very easily assign the policies you create to specific groups of devices. Remote and bulk configuration assignment speeds up the whole process of deploying devices and also improves the management of the company’s growing fleet of equipment. The use of policies eliminates the need to manually enter settings and allows you to fully control and quickly update them from the console. As a result, it saves time, eliminates errors, and enables configuration consistency – thus reducing security vulnerabilities.

Assign permissions according to job titles
Assigning policies to groups also allows restriction leveling, i.e., imposing greater or lesser limitations that can reflect permissions based on specific positions. Suppose the organization’s security policies change or new legal directives emerge. In that case, Proget allows all or selected policies to be quickly modified to comply with current regulations. Privilege management can also prove very useful when a device changes users, and the company’s policy suite needs to be updated.
Enforce compliance with rules and procedures
Policies make it possible to impose, enforce, and thus comply with rules set by the organization or required by law. They also reduce common security oversights, such as not locking a device, using too weak passwords, forgetting to change them, and others. This, in turn, contributes to ensuring a higher level of protection for corporate equipment, the data stored on it, and the infrastructure to which corporate devices connect, thus eliminating the most common reason for security breaches in companies.

What will your next step be?
Start free trial of the system and arrange a consultation with an expert
to discuss how Proget MDM will help meet your specific business needs.





